5 Things You Should Know About Docker Registries in Artifactory
As a universal artifact repository manager, Artifactory is, among other things, a fully fledged Docker registry. In addition to storing and managing Docker images, Artifactory also offers extensive integration with your CI pipeline, supports authentication through external providers, high availability, massively scalable storage and is constantly updated to support the latest Docker client version and APIs.
To help you become an Artifactory power user, I’ve compiled a few use cases and FAQs that our customers have that come up when using Artifactory Docker registries. So here are 5 tips that can help you orchestrate your Dockerized environment:
Docker Registry Cleanup
In the course of developing your Dockerized application, you might run builds quite frequently and generate an extensive number of tags (versions). Dealing with the cleanup and retention manually can be somewhat ineffective. To help you keep your Docker registries nice and clean, Artifactory has an internal mechanism limiting the number of your tags (versions) for particular images that’s really easy to configure. You might also be interested to know that Artifactory’s garbage collector automatically cleans up any unreferenced Docker layers. These are layers that are not used by any image as a result of Docker tags being removed (whether due to the limit on tags or by intentional deletion). And all of this “spring cleaning” of your Docker registries is done transparently and automatically, behind the scenes, without any downtime.
Docker Builds Exposed
One of Artifactory’s clearest differentiators is its exhaustive build information enabling fully reproducible builds. While this is not news for other package formats, it is for Docker. The new Docker Build Info support for Jenkins allows full traceability of your Docker images produced through Jenkins CI server. Stay tuned for more about that in one of our upcoming posts.
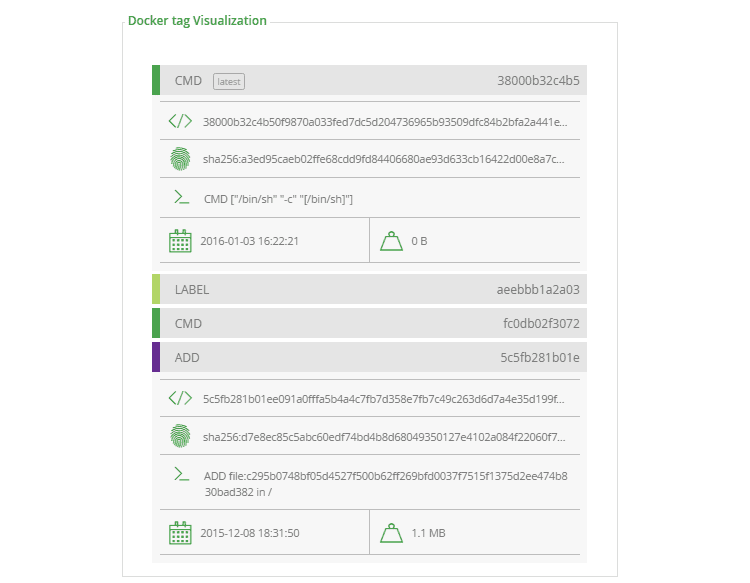
Docker Images Exposed
Artifactory looks deep into the images stored in your Docker registries. Select any image in Artifactory’s tree browser and select the Docker Info tab. Artifactory shows the entire history of commands used to select the tag along with its digest, similar to what you would get running docker history:
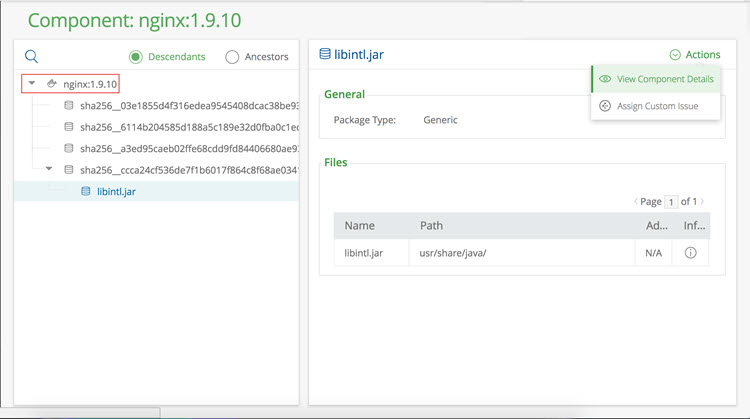
Through Artifactory’s integration with JFrog Xray, you can expose Docker images from another angle. Xray performs a deep recursive scan on the images in your Docker registry and then does an impact analysis to determine which components are infected with a security vulnerability or any other issue detected by Xray. In the example below we see a component with a vulnerability that is included in the nginx Docker image. Without this impact analysis it would have been very difficult to detect which Docker images were affected.
Controlling Image Downloads
You may block images from being downloaded from your Artifactory Docker registry if the image hasn’t yet been scanned by Xray and been given the stamp of approval that it has no known vulnerabilities or issues . You can even make sure your Docker images comply with any OSS license policies your organization may have. And if you are using Arftifactory’s distribution repository to distribute your Docker images outside your organization through Bintray, you can control downloads to the level of specific Docker tags to make sure sure only entitled users can consume your images. To learn more about controlling downloads, check out the details on download blocking.
Authentication Methods
Artifactory supports many ways to manage and authenticate users, groups and permissions such as LDAP/Active Directory, OAuth, SAML and others. However, this creates a dependency on the external authentication provider which you may not always want. For example, you don’t want your Docker builds to grind to a halt if your LDAP server (or SAML, or whatever you’re using) is unavailable. To remove this dependency, you can authenticate your build server’s user by creating an API key for it and authenticate using that. You can create an API key through the the User Profile page in Artifactory, or via the REST API. The API key can be passed in as an X-JFrog-Art-Api header element in the API call (as shown in the example below) or it can replace the password when using basic authentication.
$ curl -X GET “https://<serverName>:8081/artifactory/api/docker/<RepoName>/v2/<Image>/tags/list” -H “X-JFrog-Art-Api:AKCp2UNCt2ENCPMX2LUQn2kkYfpDm2E4LgE6EKR3JEsWDXGbJxY18LsEvkYAGWmnKLddV88Hw”
Learn more about using using Artifactory as your Docker Registry.
Still not using Artifactory as your Docker Registry? Get a free trial.



